Random Uniform Source: Difference between revisions
No edit summary |
(Benchmark link added) |
||
| (3 intermediate revisions by 3 users not shown) | |||
| Line 2: | Line 2: | ||
Uniform Random Number Generator | Uniform Random Number Generator | ||
Generates a number of samples of random numbers of [min, max) meaning the max value won't be included. Repeat samples if specified. Great for creating bytes of information for a modulator. | |||
Ex: With min=0 and max=2, the sequence 01110101... will be generated. | |||
Supports an output of type int, short, and byte. | |||
This block differs from [[Random Source]] in the pseudorandom number generator used. This block implements the [https://xoroshiro.di.unimi.it/xoroshiro128plus.c XOROSHIRO128+] algorithm in C++, which [https://prng.di.unimi.it has been shown] to be require much less processing time than the [https://en.wikipedia.org/wiki/Mersenne_Twister MT19937]¹ algorithm used by Numpy in [[Random Source]], but that only fills a vector which is then repeated at runtime, whereas XOROSHORO128+ only repeats after 2<sup>128</sup>-1 bits. | |||
Since the [[Random Source]] just repeats a relatively short vector of precomputed random numbers, '''if in doubt, prefer Random Uniform Source''' (this block). | |||
== Parameters == | == Parameters == | ||
| Line 18: | Line 26: | ||
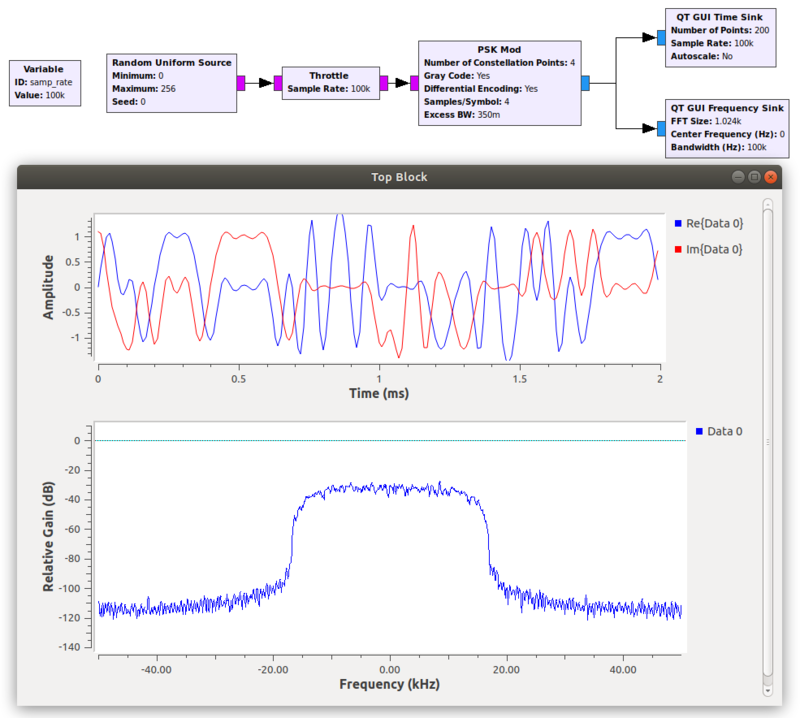
[[File:Random-uniform-source-ex.png|800px]] | [[File:Random-uniform-source-ex.png|800px]] | ||
== Source Files == | |||
; C++ files | |||
: [https://github.com/gnuradio/gnuradio TODO] | |||
; Header files | |||
: [https://github.com/gnuradio/gnuradio TODO] | |||
; Public header files | |||
: [https://github.com/gnuradio/gnuradio TODO] | |||
; Block definition | |||
: [https://github.com/gnuradio/gnuradio TODO] | |||
== Computational Performance == | |||
See [[Random_Source#Computational_Performance]] | |||
---- | |||
¹ The disadvantage of the xoroshiro128+ algorithm is it fails the Hamming-weight dependencies test after 5TB of generated values and thus is unsuitable for generating many random values if "optimal pseudo-randomness" is required. For that to be theoretically relevant, you would need to use more than 5 TB of RAM with pre-generated random numbers in [[Random Number Source]], and even then, the effects are not noticable unless you're looking for cryptographic weaknesses or similar. | |||
Latest revision as of 16:08, 13 January 2022
Uniform Random Number Generator
Generates a number of samples of random numbers of [min, max) meaning the max value won't be included. Repeat samples if specified. Great for creating bytes of information for a modulator.
Ex: With min=0 and max=2, the sequence 01110101... will be generated.
Supports an output of type int, short, and byte.
This block differs from Random Source in the pseudorandom number generator used. This block implements the XOROSHIRO128+ algorithm in C++, which has been shown to be require much less processing time than the MT19937¹ algorithm used by Numpy in Random Source, but that only fills a vector which is then repeated at runtime, whereas XOROSHORO128+ only repeats after 2128-1 bits.
Since the Random Source just repeats a relatively short vector of precomputed random numbers, if in doubt, prefer Random Uniform Source (this block).
Parameters
- minimum
- defines minimal integer value output.
- maximum
- output values are below this value
- seed
- for Pseudo Random Number Generator. Defaults to 0. In this case current time is used.
Example Flowgraph
Source Files
- C++ files
- TODO
- Header files
- TODO
- Public header files
- TODO
- Block definition
- TODO
Computational Performance
See Random_Source#Computational_Performance
¹ The disadvantage of the xoroshiro128+ algorithm is it fails the Hamming-weight dependencies test after 5TB of generated values and thus is unsuitable for generating many random values if "optimal pseudo-randomness" is required. For that to be theoretically relevant, you would need to use more than 5 TB of RAM with pre-generated random numbers in Random Number Source, and even then, the effects are not noticable unless you're looking for cryptographic weaknesses or similar.